
Cybersecurity
According to IBM’s 2022 Data Breach Report, critical infrastructure organizations face an average cost of USD 4.82 million for a data breach, which is USD 1 million higher compared to other industries. These industries encompass financial services, technology, energy, transportation, communication, healthcare, education, and the public sector. Out of these organizations, 28% experienced destructive or ransomware attacks, while 17% encountered breaches due to compromised business partners.
How AI is opening ways in reducing Security Breach Cost and Attack Dwell Time?
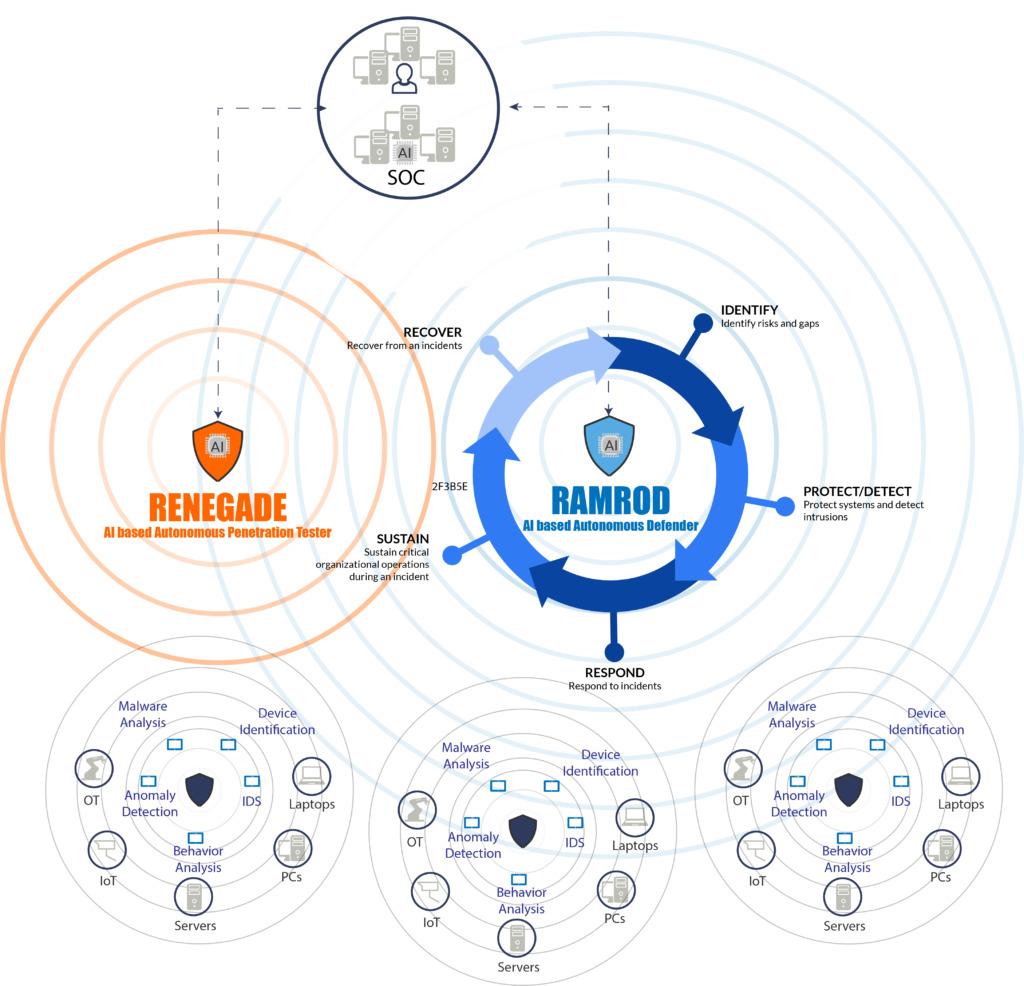


- Organizations that have fully implemented security AI and automation systems enjoy significant cost savings during breaches, with a difference of USD 3.05 million compared to organizations without such systems. The study found that breaches at fully deployed organizations averaged USD 3.15 million, while those without any deployment reached USD 6.20 million, representing a 65.2% reduction in breach costs, the highest recorded in the study.
- Companies with fully deployed security AI and automation systems experience a 74-day reduction in the breach lifecycle, the time taken to identify and contain breaches, compared to those without such systems. The average breach lifecycle for organizations with security AI and automation is 249 days, whereas it extends to 323 days for those without.
- The adoption of security AI and automation has increased by almost 20% in just two years, rising from 59% in 2020 to 70% in 2022. A separate report by MTrend in 2021, based on the FireEye real-time attack map, reveals that the introduction of AI-based strategies has significantly reduced the attack dwell time. The dwell time, representing the number of days an attacker remains undetected within a victim’s environment, has seen a drastic reduction.
- In 2020, the global median dwell time fell below one month for the first time, with organizations now detecting incidents within just 24 days. This is a remarkable improvement from 2011 when the average was 416 days and more than twice as fast as 2019, which took 56 days to detect incidents.


